SSH compression: how to zip and unzip via SSH
In this article, we are going to show you how to zip and unzip via SSH. You will learn about the compression and extraction methods on your server for...
How to set up an FTP server on an Ubuntu VPS
File Transfer Protocol (FTP) is a method for sharing files between computers over the internet using the TCP/IP protocol. It incorporates a...
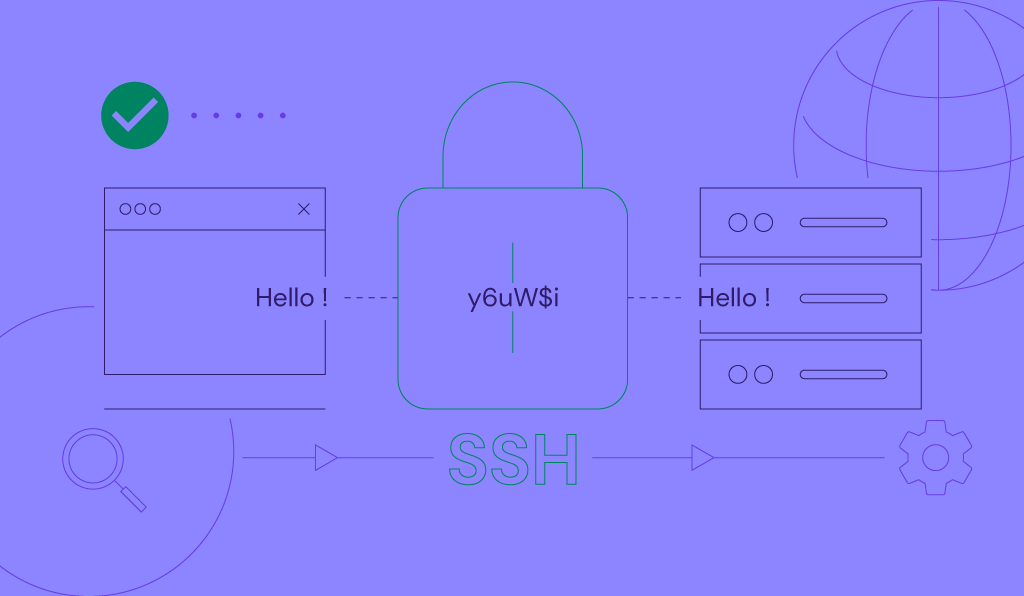
What is SSH? Understanding SSH and its encryption techniques
SSH (secure shell protocol) is an encrypted protocol for accessing and managing remote systems, such as a server, over the Internet. It’s...
How to use the Linux locate command to find any file
If you’re using Linux for the first time, you might be confused about how to search for files and directories on your computer. There are two...
How to install ClamAV on CentOS 9 Stream
Do you want to protect your VPS from dangerous malware and viruses? You can easily do that by installing an antivirus. There are plenty of options out...
How to check disk space usage in Linux
In Linux, monitoring disk space is crucial for maintaining system performance and preventing insufficient storage issues, such as system crashes, data...
How to check and list running processes in Linux
In Linux, processes are instances of running programs or commands. A single application can run multiple processes to handle different tasks. For...
How to use PuTTY to generate SSH key pairs for site security
SSH keys are one of the most secure SSH authentication options. It is definitely more secure than the usual SSH password authentication. Therefore, it...
SSH disable password login: securing your Linux VPS
The majority of people use password authentication to connect to their servers via SSH command line and do not even consider that this authentication...